What is Prisma Cloud?
Prisma Cloud is an API-based cloud service from Palo Alto Networks that connects to your cloud environments in just minutes and aggregates volumes of raw configuration data, user activity information, and network traffic to analyze and produce concise and actionable insights.
Prisma Cloud Licensing
There are two license options available with Prisma Cloud as follows:
Compute: The compute license gives you the option of hosting the Prisma Cloud service locally in your own environment
Enterprise: This is a SaaS-based offering
The Enterprise option is also further sub-divided into: Cloud Security Foundations and Cloud Security Advanced
Cloud Security Foundations
This offers the following via an agentless architecture:
- Real-time threat and misconfiguration execution for SaaS
- Compliance management
- Workload vulnerability scanning
- Infrastructure as Code (IaC) misconfiguration detection
- Least-privileged access enforcement
Cloud Security Advanced
This offers the features provided by Foundations as well as:
- Host, container and serverless runtime security
- Web application and API security
Note: Even if you’re running the Cloud Security Foundations option, some of the functionality of the Security Advanced can be purchased as add-on modules
How does Prisma Cloud work
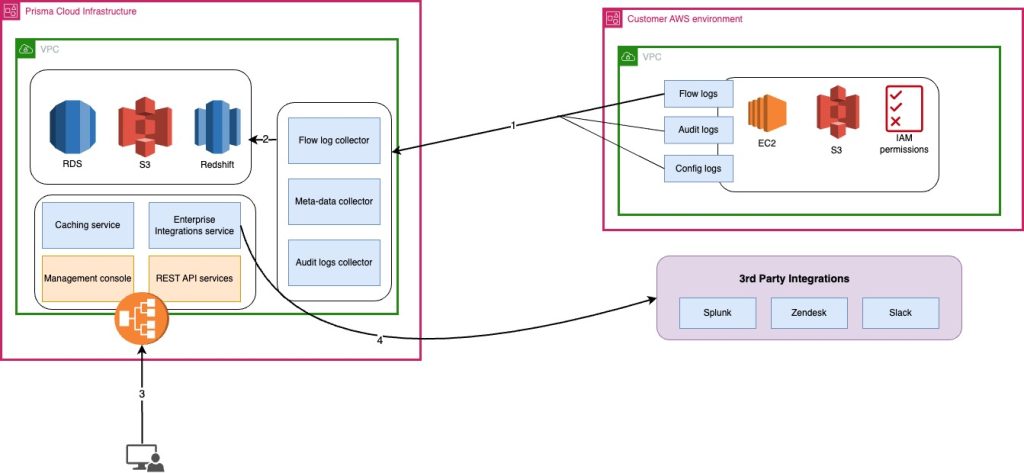
Using an AWS environment as an example, the Prisma Cloud workflow can be summarised in 4 key steps:
- Prisma Cloud ingests flow logs, config logs and audit logs from your environment
- It stores meta-data gotten from the ingested logs in encrypted RDS and Redshift instances
- From the Prisma Cloud admin console, an admin can then configure policies, integrations, and alert notifications
- Prisma Cloud then feeds data to your other 3rd party tools such as Splunk, ZenDesk etc. to aid your SOC workflow
The numbered arrows in the diagram below represents each of these steps
How to get Prisma Cloud
You can sign up to Prisma Cloud from the AWS Marketplace. There you can select whether to go with the 1-year, 3-year, or 5-year option. You can also choose the Pay-As-You-Go option. After signing up, you will receive a URL for your access to Prisma Cloud. The URL will vary depending on the region and cluster on which your tenant is deployed.
Enable Inbound Access from the Prisma Cloud Console
In order for Prisma Cloud to connect to your cloud environments for monitoring, you must allow inbound access for Prisma Cloud’s public IPs to your environment. Prisma Cloud uses specific NAT gateway addresses. To access the Prisma Cloud console, you also have to ensure you have necessary policies in place to allow connectivity to Prisma Cloud’s public IPs.
There are two parts to the Egress access required:
- You need to allow access to Prisma Cloud and the API for any integrations enabled between Prisma Cloud and your incident response workflows
- You need to allow access from your agentless deployments and the Prisma Cloud defenders to communicate with the Prisma Cloud Compute console.
The IP address for each access can be found here.
Note: Your Prisma Cloud URL indicates the region where your tenant is deployed. For example, if your Prisma Cloud URL is https://app2.prismacloud.io, your tenant is on app2. In order to find the region, log on to the Prisma Cloud console and navigate to Compute > Manage > System > Utilities. On this page, you’ll find ‘Path to Console‘ in a format that looks something like: https://us-west1.cloud.twistlock.com/us-xxx. This indicates that your Compute console region is us-west1.
Account Onboarding to Prisma Cloud
To onboard your cloud accounts, ensure you have configured the appropriate permissions in your cloud accounts for Prisma Cloud to authenticate and retrieve data. You will normally need to create a Prisma Cloud role with either read-only access to your traffic flow logs or with limited read-write access to remediate incidents.
When onboarding an account or AWS organization to Prisma Cloud, you will need to select the ‘Security Capabilities and Permission‘ you want to enable for the AWS account/organization. The capabilities are grouped into:
- Foundational (enabled by default): this grants permissions to scan cloud resources and ingest data
- Advanced: on top of the foundational capability, this allows you proactively control your cloud operations and identify and remediate issues.
Depending on which one you select, a Cloud Formation template (CFT) is generated that includes the associated permissions for the Prisma Cloud role. By default, the CFT enables the ingestion of configuration data, Amazon S3 flows logs, AWS Cloudtrail logs and Amazon Eventbridge only. If you want Prisma Cloud to ingest VPC flow logs and other integrations such as Amazon GuardDuty, you must enable those services on the AWS Management console.

