In this post, I summarize the AWS fundamental building blocks covered in the AWS Solutions Architect Associate exam.
AWS Building Blocks
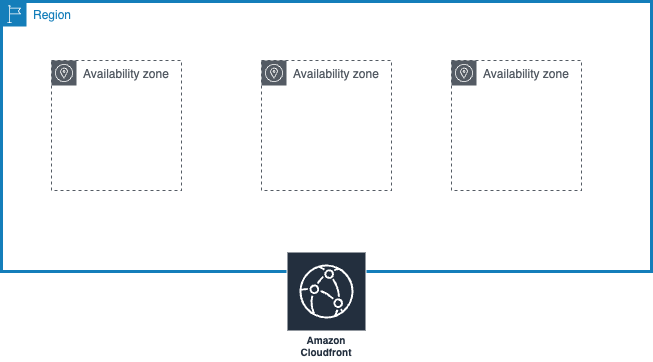
- A region is a physical location in the world that consists of 3 or more availability zones.
- An Availability Zone (AZ) is one or more discreet data centers, each with redundant power, networking, and connectivity – housed in separate facilities
- Edge locations are endpoints for AWS that are used for caching content. Typically, this consists of CloudFront, Amazon’s content delivery network
Well-Architected Framework Pillars
There are 6 pillars of the well-architected framework. These are:
- Operational Excellence: running and monitoring systems to deliver business value, and continually improving processes and procedures
- Performance Efficiency: Using IT and computing resources efficiently
- Security: Protecting information and systems
- Cost Optimization: Avoiding unnecessary costs
- Reliability: Ensuring a workload performs its intended function correctly and consistently when it is expected to
- Sustainability: Minimizing the environmental impacts of running cloud workloads
Identity and Access Management (IAM)
- Permissions are controlled/assigned in IAM using policy documents, written in JSON
- IAM policy documents can be assigned to groups, users or roles
- IAM does not work at a regional level. It works at a global level
An example policy document can be seen below:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}This is a simple policy document that gives full admin access privileges.
- By default, when you create a user that is not a member of a group, that user has no permissions to do anything on the AWS Console
- To allow programmatic access to AWS (i.e CLI or API access), you need to create an access key. As part of the access key creation, a Secret Access Key is also generated. These two values, used together, grant programmatic access to AWS
- If you already manage your user identites outside of AWS, for example a corporate user directory, you can use ‘Identity Providers’ in AWS to give those external user identities permissions to use AWS resources in your account. Your external identity provider (IdP) provides identity information to AWS using either OpenID Connect (OIDC) or SAML 2.0
A useful acronym to remember when working with IAM policies is PARC. Each letter is explained as follows:
- Principal: the entity that is allowed or denied access
- Action: the type of access that is allowed or denied
- Resource: AWS resources the action will act upon
- Condition: conditions for which the access is valid
The following additional elements are also found in IAM policies:
- All IAM policies have an ‘Effect’ field which is set to either ‘Allow’ or ‘Deny’
- ‘Version’ field defines which IAM service API version to use when evaluating the policy. For example,
"Version": "2012-10-17" - ‘Statement’ field consists of one or many JSON objects that contain the specific Action, Effect, Resource and Condition fields
- ‘Sid’ (statement ID is an optional identifier for a policy statement)
Note: Identity based policies do not affect the root user, so actions taken by the root user account are implicitly allowed.
